💬❤️ Enable donors to give to nonprofits via their mobile phones.
Inside: The Basics of Text-to-Give, Text-to-Give Pro Tips, and Text-to-Give Platforms and Tools
Nonprofit leaders are tasked with capturing the attention of potential supporters and creating a convenient experience that invites them to continue donating. That’s why fundraising methods like text-to-give are so popular!
In addition to boosting revenue, text donations enable nonprofits to secure long-term support for their cause via boosted donor engagement and retention. In this guide, we’ll cover all the must-know information and vital tips for better text-to-give fundraising, including:
- Text-to-Give Fundraising FAQs
- How to Launch a Text-to-Give Fundraiser
- 10 Text-to-Give Fundraising Tips
- Best Text-to-Give Fundraising Platform and Tools
Text-to-give is an effective giving vehicle that organizations shouldn’t overlook. Ready to enhance your fundraising plan and boost donor engagement? Let’s dive in!
Text-to-Give Fundraising FAQs
What is text-to-give fundraising?
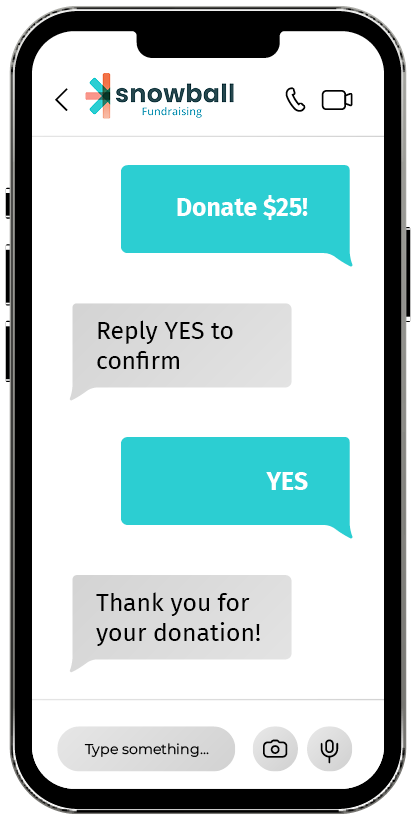
Text-to-give fundraising, or text-to-donate, is a form of fundraising that enables supporters to give to nonprofit, faith-based, and political organizations through text messaging. It allows donors to give anytime, anywhere in only a few seconds.
The process is simple:
- Your organization is assigned a phone number by its text-to-give provider.
- A supporter texts a keyword (also known as a trigger word) and a donation amount to your organization’s phone number. Alternatively, donors may send only the trigger word and receive a link to your mobile donation page in response, where they’ll submit their gift.
- You designate these donations to go toward your annual fund or to a specific campaign.
That’s it! Mobile giving is easy for both your organization and your donors. Let’s look at a few other ways this modern fundraising approach can transform your fundraising.
How much does text-to-donate cost?
The cost varies per platform, but typically, it’s based on a flat fee amount in addition to a fixed processing rate for credit cards. For the most cost-effective investment, choose a platform that gives you unlimited text and text-to-give keywords and bypasses mobile carrier fees (like Snowball!)
What’s the standard gift size?
According to Nonprofit Source, the average donation size for text-to-donate campaigns is $107. Not only can these donations be substantial, but text-to-give enables easy setup for future recurring donations. In other words, you may encourage ongoing support and gifts from donors without making additional donation appeals.
Is text-to-give secure?
With a PCI-compliant text-to-give provider like Snowball, your mobile gifts will be in safe hands. We use authentication and tokenization to protect your donors’ sensitive information, such as billing information and addresses.
What types of nonprofits host these fundraisers?
Countless nonprofits use mobile fundraising and text-to-give to drive support for their causes, including:
- Faith-based organizations: Most religious organizations also encourage their members to take out their phones and use text-to-tithe in addition to traditional collection plates.
- Health and wellness organizations: Healthcare organizations can use mobile fundraising as part of their grateful patient programs and annual funds.
- Animal rights organizations: Animal rights charities inspire supporters to give via their mobile devices by sending out cute pictures, GIFs, and videos of animals.
- Educational advocacy organizations: With the increase in popularity of text-to-donate and mobile giving software, one of the best ways teachers can improve their classrooms is to launch their own online fundraisers. It’s also a great resource for PTAs looking to launch a new school fundraiser.
- Environmental awareness organizations: Text-to-give is a paper-free giving method, meaning environmental awareness and advocacy groups are increasingly imploring donors to use their mobile devices.
- Arts and cultural organizations: Museums, theaters, zoos, and galleries tend to use methods like ticket sales and membership programs to raise money. A growing trend toward using mobile donation software provides more convenient solutions to interested donors.
Any type of nonprofit can benefit from mobile fundraising and any type of supporter can leverage the convenience of donating from their cell phones.
What are the pros and cons of hosting a text-to-give fundraiser?
When someone tells you there’s good news and bad news, which would you rather hear first? Since the list of text-to-give cons is so short, we’ll get the disadvantages out of the way first:
- Donation amount cap: Some providers (not Snowball!) may put a limit on how much donors can give via text-to-donate.
- Engagement limitations: The simplicity of text-to-give also means donors provide minimal information and spend less time interacting with your nonprofit.
However, the pros vastly outweigh the cons of text-to-give fundraising.
As one of the most effective donation methods, text-to-give empowers nonprofits of all sizes to reach new fundraising heights. Since so many of your supporters own mobile devices, incorporating text-to-give into your fundraising strategy allows your nonprofit to tap into the growing influence of mobile usage:
- 97% of Americans own a cell phone, making it the preferred method of communication. Because text-to-give uses technology that most donors and fundraisers already use on a daily basis, they’ll be more inclined to take the time to send a quick donation to their favorite organization.
- 57% of nonprofit website traffic came from mobile devices last year, meaning mobile giving aligns with the way potential supporters are already engaging with your nonprofit’s information. In fact, 1 in 4 donors use mobile devices to discover nonprofits they were previously unaware of.
- Since 91% of Americans look at their cell phones around 80 times a day, mobile giving is an easy way to keep donors involved and excited without slowing them down. Plus, donors are more likely to pay attention to mobile giving requests because 90% of text message reminders are read in 3 minutes.
Mobile fundraising is one of the easiest ways donors can contribute to your organization. It completely streamlines the donation process by eliminating the need to use a desktop, a laptop, or even direct mail. Donors can even opt to set up recurring donations and continue showing their support.
The simplicity of text-to-give also makes it a great way to run concurrent fundraising initiatives. For example, you can promote and accept text donations at your in-person auction to maximize fundraising revenue and awareness of your nonprofit’s programs. This fast, easy, and engaging donation process lays the groundwork for stronger donor relationships.
How to Launch a Text-to-Give Fundraiser
If you’re sold on text-to-give fundraising and ready to get started, you may be thinking, “What now?” Let’s look into the steps you need to take to launch your campaign.
1. Implement a text-to-give strategy.
First, you’ll need to determine the logistics of your fundraiser. To implement text-to-give in your fundraising strategy, answer the following questions:
- Who will be in charge of running your text-to-give campaign?
- What will the donations support? Are they for a specific project?
- When will you launch and close your text-to-give campaign? When do you expect to reach your donation goal?
- Where will you promote your campaign and post updates?
The answers to these questions will guide the rest of your planning. For example, knowing what project will be supported by text-to-give donations can help you craft compelling marketing materials to promote your mission.

2. Set attainable goals.
Donors should know exactly how their hard-earned money is helping, and so should your nonprofit! Clearly define goals for your text-to-give campaign to determine where the money will go. Use the SMART goal framework to ensure your goals are:
- Specific
- Measurable
- Attainable
- Relevant
- Time-bound
After you determine your objective and launch your campaign, you’ll need to keep your supporters updated on its progress. Use a fundraising thermometer to show how donors’ gifts contribute to the bigger picture, incentivizing their participation. Feature your thermometer on your donation page and website and share updates on social media.
3. Put a marketing plan in place.
Once you’ve straightened out the fine fundraising details, it’s time to share your campaign with the world! Regularly update your supporters and encourage them to share your text-to-give campaign with their networks. To spread the word, consider the following:
- An email newsletter with simple guidance on how donors can get started.
- A press release emphasizing your organization’s role in the community.
- An announcement on your website such as a video from your nonprofit’s team.
- Search engine marketing to draw attention to your campaign page.
- Social media posts that supporters can share with their followers.
Seek out influencers to help boost the visibility of your text-to-give campaign. By recruiting influential advocates, you’ll inspire new donors to trust you and contribute.
4. Collect data on campaign progress.
Just like any other campaign, you need to track (and act on) key analytics. Remember to track the following:
- Individuals’ text-giving frequency
- Average text donation size
- Marketing channel engagement (website click-through rate, social media engagement rates, etc.)
- Donor information (name, mailing address, etc.)
By tracking this data, you’ll gain a better sense of what’s working and what’s not. Which marketing channels are receiving the most engagement? What about the least engagement? Is your campaign messaging actionable enough? Make strategy adjustments according to what you learn.
10 Text-to-Give Fundraising Tips
As you become more experienced with mobile giving, employ a more advanced approach to yield the best results. Consider these tips to make the most of your campaign:
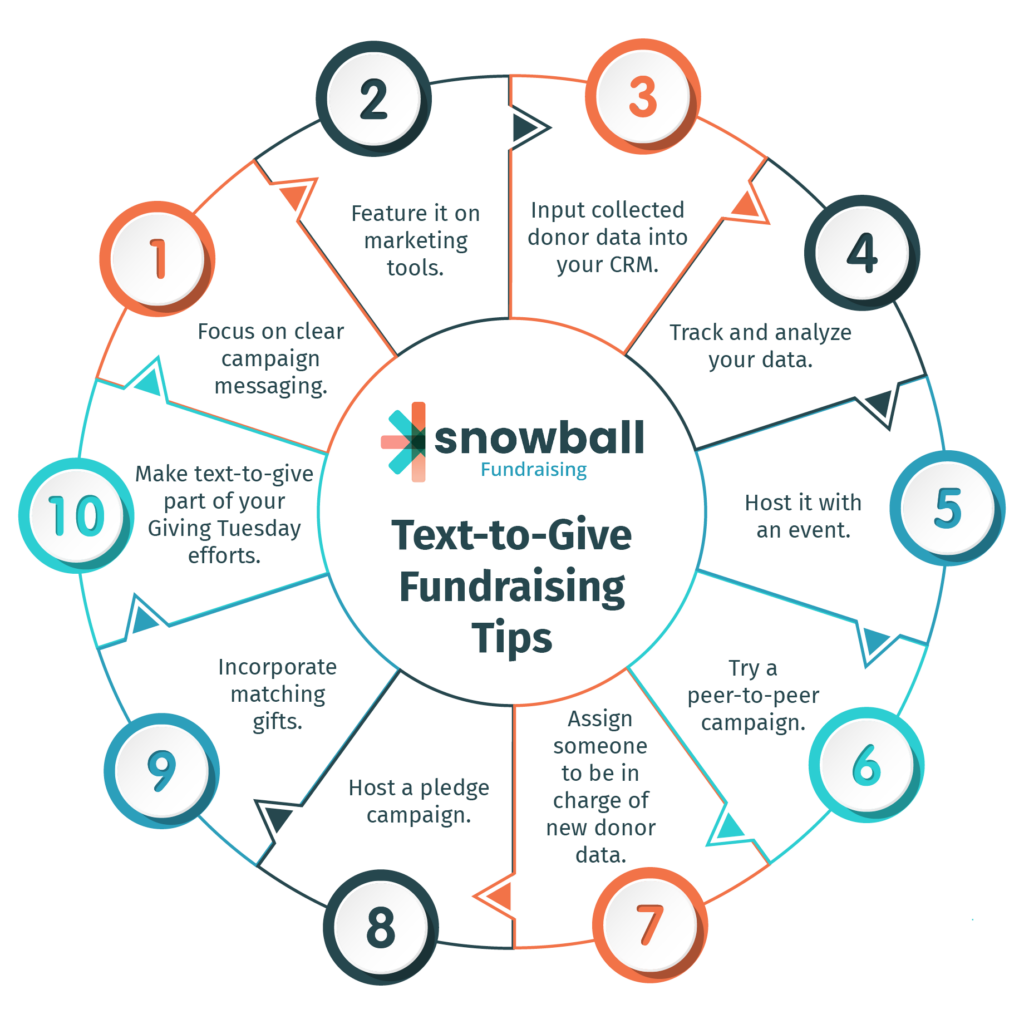
1. Focus on clear campaign messaging.
Before you can explain how to give, you’ll need to convince donors why they should give. Be clear about the need for your campaign and its goals by providing:
- Specific and actionable reasons for your campaign
- The importance of your cause (and why it’s worth supporting)
- A sense of purpose through the act of giving
Take the Red Cross’s disaster relief efforts for example:
The organization gives numerous, specific examples of its disaster relief efforts, even giving a specific example of an individual beneficiary. Then, it explains what is accomplished with donor gifts and even gives some impressive statistics about the nonprofit’s reliance on volunteer work.
2. Feature it on marketing tools.
Across all your communications, actively promote your organization’s number and keyword with calls-to-action. Adjust your tactics according to the platform:
- Direct mail will need eye-catching inserts to capture the attention of recipients. You can also include QR codes to encourage supporters to move online.
- Emails can highlight the number and keyword subtly in your email signature or loudly with a pop of color.
- Social media posts provide opportunities to use visuals, such as compelling photos and videos.
Feel free to get creative! Most importantly, vary your approach across platforms so that your text-to-give campaign appeals to all of your different audiences.
3. Input collected donor data into your CRM.
Make sure to input donors’ names, phone numbers, email addresses, and billing addresses into your existing database. This way, you can incorporate them into your future fundraising efforts.
4. Track and analyze your data.
As with any fundraising activity, you should keep track of your performance. Track text-giving frequency and average text donation size to help inform your future donation appeals. Make note of any trends as well as any shifts away from those trends.
5. Host it with an event.
Incorporate text-to-give into your other fundraising events to maximize revenue. For example, you might hang engaging flyers with your text-to-donate number and shortcode around the venue at your auction.
The right event management software will streamline multiple capabilities, making it easier than ever for you to host concurrent campaigns. That way, you can keep your event tasks and text-to-give fundraiser information all in one place.
6. Try a peer-to-peer campaign.
A peer-to-peer campaign isn’t just a great way to spread the word about your cause; it’s a great way to spread your text-to-donate number, too. Encourage your volunteers to create their P2P pages like they normally would. Then, when they share their fundraising pages with their social networks, they can advertise your text-to-give number and shortcode.
7. Assign someone to be in charge of new donor data.
When you run a text-to-give campaign, you’ll be flooded with new donor information. Assign a staff member to take charge of the data. Then, put processes in place to account for common concerns, such as what to do if new data differs from old data and how to handle duplicate information.
8. Host a pledge campaign.
A pledge campaign is a great twist on traditional text-to-donate campaigns. Since the average mobile donation pledge for fundraising events is $167, your organization stands a good chance of boosting donations.
Have volunteers create their pledge pages. Then, they can share your organization’s text-to-donate information. Supporters will have the option to pledge their support with the pledge page or donate right then by texting their gift.
9. Incorporate matching gifts.
To give via text, donors will have to give you their contact information. This is the perfect opportunity to email them about matching gifts because their text donation might be eligible for a match through their employer.
Reach out to your text-to-donate participants and encourage them to explore matching gift opportunities through their employer. Once supporters submit a request for their employer to match their gift, your nonprofit could receive another donation!
10. Make text-to-give part of your Giving Tuesday efforts.
Giving Tuesday (and other time-based initiatives) represents a great chance to encourage donors to expand their giving as a result of an urgent push. Because there’s a limited time frame, donors are motivated to act fast, and texting their donations is the fastest way to give.

Best Text-to-Give Fundraising Platform and Tools
The key to hosting a successful text-to-donate fundraiser is having the right tool to facilitate it, like Snowball. Snowball Fundraising is a mobile-optimized fundraising suite for any organization, nonprofit, or church.
At Snowball, we have a simple solution for giving on the go—one that doesn’t require donors to have a credit card handy 24/7. Our text-to-give platform enables donors to give wherever they are, whenever they want. All it takes is a couple of taps: one to send a text with the donation amount and another to confirm the payment.
With our platform, you’ll receive more than the basics. Streamline all your fundraising efforts with these features:
- Unlimited inbound text messages
- Unlimited custom trigger words (or keywords)
- Instant setup
- No extra software or accounts for your donors
- Easy repeat and recurring donations
- Affordable outbound text messaging
- Text-to-bid, text-to-tithe, and text-to-ticket capabilities
Unlike other platforms, once a donor enters their information for the first time with Snowball, they never have to enter it again—even if they’re donating through another online or mobile avenue. Best of all, with our PCI-compliant technology and single-factor authentication, you’ll know your donors’ information is completely protected. Our platform is highly secure, allows donations to reach your nonprofit within a few business days, and integrates seamlessly with your other fundraising initiatives.
Additional Resources on Text-to-Give Fundraising
Remember, the great thing about a text-to-give campaign is that it can be hosted on its own or in coordination with your other events and campaigns. You’re sure to boost funds so long as you take a strategic approach and keep the donor experience front of mind.
Here at Snowball, our mission is to provide nonprofits with the intuitive tools they need to maximize fundraising success. No matter your organization’s mission, we’ve got you covered.
Check out these additional resources for more information:
- 4 Top Strategies to Boost Your Mobile Giving Potential. Looking for more tips on maximizing your mobile giving success? Check out these strategies to help your organization reach more potential supporters and increase engagement easily and quickly.
- Free Fundraising Software for Nonprofits: 15+ Providers. Digital tools can streamline crucial nonprofit fundraising tasks, but software can get pricey. Check out our favorite affordable fundraising software providers!
- Donor Stewardship: 3 Fundamentals for Growing Nonprofits. Want to explore more ways to engage your supporters and strengthen donor relationships? Learn how to effectively steward donors in this guide!

💬❤️ Enable donors to give to nonprofits via their mobile phones.
Inside: The Basics of Text-to-Give, Text-to-Give Pro Tips, and Text-to-Give Platforms and Tools